Free S/MIME certificates in 2019
Posted in daily
Tags :
TL;DR : If you need a S/MIME certificate for your personal use, avoid purchasing it from Sectigo and prefer Actalis (but please read the warning and updates below).
I have been using S/MIME (Secure/Multipurpose Internet Mail Extensions) certificates to digitally sign and encrypt my emails (or PDFs) for the last decade or so.
Wikipedia defines S/MIME as “a standard for public key encryption and signing of MIME data”.
If you don’t have your own in-house certificate authority, you can obtain individual key/certificates from a number of public certificate authorities (CA).
The number of sources of free S/MIME certificates has dried up recently. I’ve used a number of services in the past raging from Verisign, StartSSL, InstantSSL to Comodo, but currently, only Actalis offers free certificates for personal use. At the time of writing, Let’s Encrypt doesn’t offer S/MIME certificates.
Historically, only Firefox and Internet Explorer contained the cryptotools capable of generating public/private keypairs that could be certified by a CA. So, it’s important to remember to use the same browser on the same computer to both generate the keypairs and collect the certificate.
You can then export it as a .p12 file which, in turn can be imported into your Keychain or as a new Profile on iOS.
All this to say that when time came to update my certificates, I turned to the previous CA I used. Unfortunalety, Comodo have changed their name to Sectigo and no longer offer free S/MIME certificates.
My previous experience with Comodo was good, so I decided to fork out the USD$ 19.90 to purchase a new certificate. Boy, did it turned out to be a bad idea.
Giving them the money was easy enough, but the rest of the process was disastrous. Their online documentation is badly out of date and turns out to be wrong after exchanging emails with their support.
It shows that you need to use either Firefox or Internet Explorer to purchase a certificate, but turns out that Firefox doesn’t support the <keygen> element anymore, which left me wondering how to proceed on a Mac. Support told me to use Safari, eventhough warnings on their site told me not to do so. To my knowledge, this is the first time Safari is supported in this process.
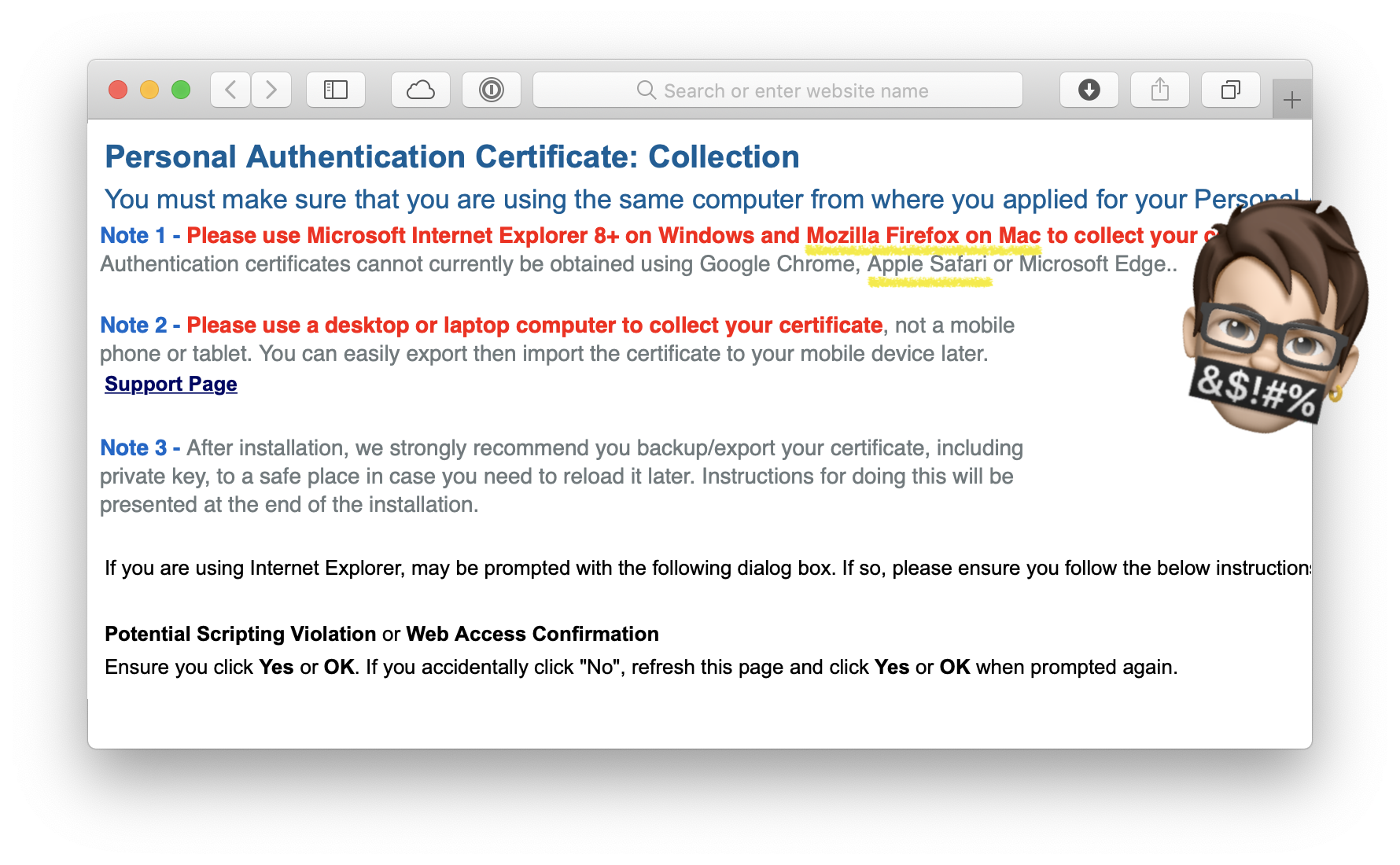
So, I started over with Safari, generating the keypairs and requesting a certificate. It took me several tries to finally receive a confirmation email with a delivery link (remember to download it from the same browser and computer). The link is composed of the associated email and a authentication token (password). This combination was rejected each time as incorrect.
Contacting support (3rd time) didn’t help as they either didn’t respond, or sent me to a knowledgebase page telling me to use Internet Explorer… They finally sent me a new confirmation email with the (sic) same information, which, guess what? Didn’t work.
I eventually opened a support ticket asking for a refund as it was now 5 days later and I hadn’t made any progress.
The cerise sur le gâteau was to receive a survey link asking how well support performed before receiving any news from my refund query. Needless to say my evaluation wasn’t exactly stellar. The refund confirmation came in 90 minutes later.
This morning, I generated 3 free S/MIME certificates in a matter of minutes with Actalis and I’m good to go for another year.
Will I go through all these hoops next year? If Actalis still offers free certificates, probably, otherwise…probably not (see update below) Yes, I still am (2021).
It’s worth noting that the Electronic Frontier Foundation announced critical vulnerabilities in S/MIME called EFAIL which enables the content of an attacked encrypted email to be transmitted to the attacker in plain text by a vulnerable email client. Now, will the vendors fix it?
Over the course of writing this post, I discovered that the <keygen> element is deprecated, and its use no longer recommended. There is a W3C Web Cryptography API proposal.
Dec 19th, 2019 important update
An issue with Actalis S/MIME certificates was brought to my attention by Hendrik Schweppe that I initially overlooked : the private key is generated on Actalis’ servers:
If Actalis stores it, the company is basically able to decrypt the encrypted mails. Since the private key is created by the provider, you have to trust the provider Actalis, which defeats the whole purpose of a “private key”.
This is also reported by Frank Zöchling in a post on Actalis certificates.
Dec 7th, 2021 update
Someone who prefers to remain anonymous reached out to Actalis to inquire about the private key generation :
The CA is by definition a trusted third party: PKIs work on this assumption. Actalis is a TSP and undergoes an annual compliance audit by independent verification bodies, and the audit reports also cover S/MIME certificates. Turning to the specific case of S/MIME certificates: in the policy that applies to these certificates and that users declare having read and accepted before requesting the certificate, it is clearly stated that Actalis does not store the user’s private key: (§3.2.2) The CA does not retain the Subscriber’s private key after having sent it to the Subscriber.

Comments and responses
03 Dec 2019